Today, SaiFlow is excited to announce a powerful new capability for energy infrastructure security: the ability to create custom detection rules that understand both network behavior and energy context.
Security teams can now build their own threat detection logic, tailored to their unique operational patterns, and deploy them across their entire infrastructure in minutes.
Within SaiFlow's Threat Detection capabilities, three complementary engines work together to protect your infrastructure.
Now, with the Custom User-Defined Rule Engine, you extend this protection with your own operational expertise. While our AI and rule-based engines catch known threats and anomalies, your custom rules address the specific vulnerabilities unique to your deployment. This combination - AI-driven detection, proven threat signatures, and your domain expertise - creates the most comprehensive energy runtime security available.
The breakthrough here isn't just custom rules - it's custom rules with energy context. By correlating OCPP, Modbus, OPC communications with actual kilowatt consumption, voltage readings, and operational telemetry, these detections reveal attacks that pure network monitoring would miss entirely. Your security team becomes empowered to translate operational insights directly into active protection, without waiting for vendor updates or generic pattern matching to catch up with your reality.
Why Your Energy Operation Needs Your Detection Rules
Every energy operation represents a unique ecosystem of equipment, protocols, and operational patterns. A solar farm's inverter communication patterns differ vastly from a wind turbine's SCADA signals, just as a public charging station's usage profile bears no resemblance to a battery storage facility's charge-discharge cycles. This diversity isn't a weakness - it's the reality of modern distributed energy infrastructure.
Traditional cybersecurity approaches fail here because they lack energy context. They can monitor OCPP messages but can't correlate them with actual energy delivered. They see Modbus commands but don't understand if the resulting power flow makes sense. They detect OPC traffic anomalies but can't determine if the reported values align with physical possibilities given current weather conditions or grid demand.
This is where custom energy runtime rules become essential.
When you can define detection logic that says, for example: "Flag when Modbus commands change inverter parameters outside our operational envelope during peak production", you're securing your actual operation, not just your network perimeter.
Building Energy-Aware Detection Rules
SaiFlow's visual detection-rule builder transforms your operational expertise into active threat detection without requiring programming knowledge.
The interface speaks the language of energy operations - you work with charging sessions, power readings, and energy IoT equipment states, not packets and ports.
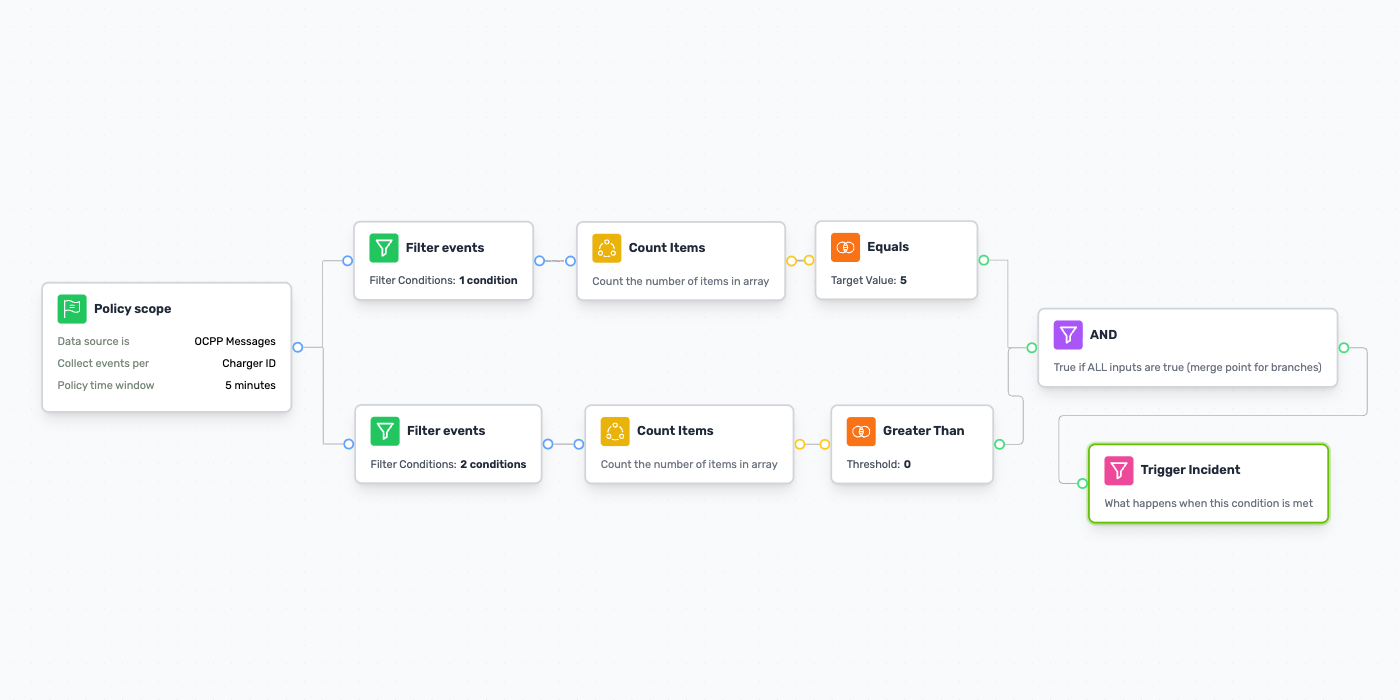
To demonstrate the capabilities of the detection-rule builder, let’s look at an example:
“DoS attack detected: Excessive OCPP Availability Requests Targeting a Single Charging Station”.
This rule is designed to trigger when a charging station receives an unusually high number of ChangeAvailability or UnlockConnector OCPP commands from the CSMS, signaling a potential attempt to disrupt or manipulate the station’s availability.
The next step is setting your monitoring scope (Defined by the Source node). Here you define what you're monitoring: charging sessions, OCPP communications, Modbus registers, or energy telemetry streams.
Define your time window - from minutes for rapid attack detection to hours for pattern-based threats. Choose how to group your analysis: by site, by equipment ID, or by customer account. This flexibility lets you create rules that match your operational reality.
Building detection logic is just as intuitive. The rule operations palette lets you construct highly complex queries with ease. The visual flow clearly shows your detection logic, making it easy to validate and communicate with stakeholders.
Available operations are neatly organized by category across multiple tabs (With more operations coming soon!). These operations allow you to transform the incoming data, aggregate and preform complex filtering & comparisons.
We’ll add a “Count” Aggregation node to count the filtered events within the defined time window. To complete the rule, we’ll connect a “Greater Than” comparison and set a threshold value. When the aggregated count exceeds this threshold, the condition evaluates to true, triggering an alert.
(optional) Before completing the policy and moving it to production , we can also add mitigation steps, in accordance with the CPOs internal policies, to ensure the security operations team has clear guidance for swift and effective incident response.
Deploying the detection-rule
The platform validates your rules in real-time, ensuring efficient performance across your infrastructure. Mathematical operations, thresholds, and pattern matching all execute at scale.
When you're satisfied with your logic, deployment takes seconds. Your rule immediately begins monitoring your entire fleet - whether that's hundreds or tens of thousands of assets - analyzing every transaction against your custom criteria.
When threats are detected, alerts include complete evidence: the specific events that triggered the rule, their timestamps, affected equipment, and energy metrics that confirm the threat. This context accelerates investigation and response, turning abstract alerts into actionable intelligence.
Scaling Across Your Infrastructure
Your security insights are only valuable if they protect your entire operation. With SaiFlow's custom detection-rules engine, a detection pattern identified at one site instantly scales to protect thousands of assets across your infrastructure.
Deploy your rule once, and it immediately begins monitoring every charger, inverter, battery system, and energy controller in your network - no gradual rollouts, no site-by-site configuration.
Real time updates to your defense measures ensure your energy network security evolves with emerging new threats. Discover a new attack pattern in the morning, refine your detection logic over lunch, and have it protecting your entire infrastructure by afternoon.
When firmware updates change normal behavior patterns, adjust your rules on the fly without disrupting protection. During high-risk periods - peak demand events, maintenance windows, or active incident response - tighten detection parameters instantly across all sites.
Let's examine two examples of sophisticated threats targeting energy operations that require custom detection rules:
- Case Study #1 - Authentication Bypass Exploitation
Attackers exploit maintenance codes like '00000000' or 'SERVICE' that bypass normal authentication in energy IoT protocols.- Custom Rule Definition: Maintenance code '00000000' or 'SERVICE' detected in authentication field, with a state transition to active charging within 5 minutes, with more than 10.0kWh delivered and zero payment recorded.
- Business Outcome / What was Prevented: Financial loss from unauthorized energy consumption and potential availability issues from systematic exploitation across multiple sites.
- Case Study #2 - DER Configuration Manipulation
Attackers target distributed energy resources by modifying PT (potential transformer) ratio settings in energy meters and controllers - a single parameter change that cascades into critical failures.- Custom Rule Definition: Modbus write command detected modifying PT ratio configuration outside acceptable range (e.g., deviation >15% from baseline), followed by abnormal charge/discharge cycles within 30 minutes.
- Business Outcome / What was Prevented: Equipment damage to battery storage systems, unintended energy discharge, reduced mean time to resolution (MTTR), and prevention of grid instability.
The evidence-backed alerting system ensures every detection provides actionable intelligence. When the authentication bypass rule triggers, you don't just get an alert - you see the exact sequence: maintenance code '00000000' used at 14:32, state transition to charging at 14:33, 47.3kWh delivered with zero payment recorded. When the PT ratio manipulation is detected, the alert shows the original value, the modified value, and the resulting energy flow discrepancies. This complete context transforms hours of investigation into minutes of response.
As your operation grows and evolves, your rules adapt with you. New energy IoT equipment types? Add detection logic specific to their protocols and behaviors. Expanding to new regions with different operational patterns? Create location-specific rules that understand local baselines. Changed your demand response strategy? Update the relevant rules without affecting other detections. Your security posture remains aligned with your operational reality, not frozen in yesterday's understanding.
Beyond Network Monitoring
SaiFlow's custom detection rules work alongside our native threat detection engines to provide comprehensive energy runtime security. While our platform continuously monitors for known attack patterns, zero-day exploits, and operational anomalies, your custom rules extend this protection to cover your unique vulnerabilities and attack surface. The combination creates defense-in-depth that understands both universal energy sector threats and your operation's specific risk profile.
The future of energy infrastructure is distributed, dynamic, and increasingly autonomous. Solar farms adjust production based on grid signals. Battery systems respond to price fluctuations. Charging networks balance load across sites.
This complexity creates new attack surfaces that traditional IT security tools weren't designed to protect.
Energy runtime security - built from the ground up to understand both digital protocols and physical energy flows - provides the contextual awareness needed to secure this critical infrastructure.
Secure the Future of Energy with Custom Detections
The transition to renewable and distributed energy is accelerating, bringing unprecedented connectivity and complexity to critical infrastructure. With it comes the responsibility to protect these systems from adversaries who understand their unique vulnerabilities.
SaiFlow's custom detection rules put this power in your hands - the ability to define, deploy, and adapt security rules that understand your specific operation.
Your expertise in your energy infrastructure is your greatest security asset. Transform it into active protection with rules that speak the language of kilowatts and protocols, not just packets and ports. Join the energy operators who are taking control of their security posture with detection rules as unique as their operations.
Ready to build energy-aware detection rules for your infrastructure? Contact our team for a demonstration of how custom rules strengthen your energy runtime security.

.png)